
The article tells about what there are hacker programs for "Android", what they know, what is needed for their correct work.
Every year, computer and digital technologiesare developing more rapidly. What still seemed like a fantasy a few years ago is now being realized. A vivid example is virtual reality.
Smartphones, computers, tablets, laptops -now this is not surprising. An entire generation has grown up, for which such devices are familiar, and many no longer think their lives without them. Although the older generation remembers the times when mobile phones were the size of a brick.
And modern smart phones are not for nothing called "callerscomputer ", since voice calls have long ceased to be their main destination, the Android operating system, whose share in the market of portable devices is about 60%, played a big role in this, it allows to develop almost any programs and make maximum use of the hardware. , that every year the list of various hacking tools for this system is growing.So what are the hacker programs for "Android"? This is what we'll figure out.

Before describing programs and their capabilities,it is worth recalling that they can be used only for informational purposes and only on personal wireless networks or other devices belonging directly to the user. Otherwise, some manipulations with them fall under the administrative or even the Criminal Code. Simply put, use them only at home or with friends with their consent. So what are the hacking programs for "Android" there?
Recall that if you decide to turn yoursmartphone or tablet into a device with which you can play your friends or for the sake of interest check your wireless networks for vulnerability, then you should use a Root device. Without it, most programs from the list below simply will not work.
Now let's analyze the most popular hacking programs for "Android", as there is a lot of such software.
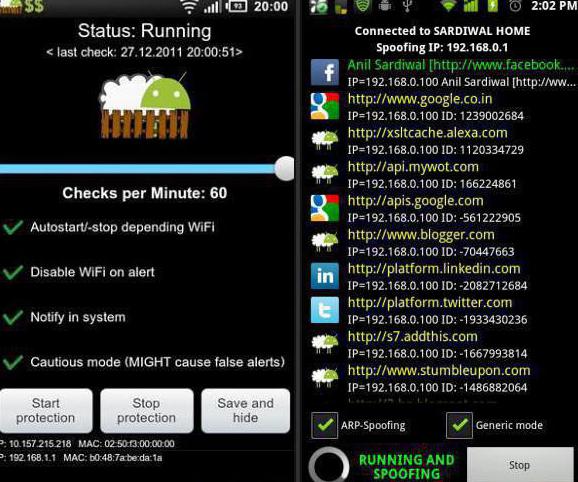
In due time this simple utility has done a lot of noise and enjoyed immense popularity among those people who were interested in information security. However, like intruders.
The meaning of this software is very simple:it is designed to "steal" web sessions and restore them in the built-in browser. To do this, you need to connect to a Wi-Fi network, start DroidSheep and just wait. When a client appears that uses authorization on some service without encryption, you will see the address of this site and you will be able to access it using the data of the "victim" authorization. The downside of this program is that you can not get the password in its pure form, only cookies.
Now consider the other free hacking programs for a smartphone or tablet.
This app is great for jokes anddraws. The idea is that the program scans the current connection to the Wi-Fi network, and if there are other clients there, you can simply turn them off, leave without the Internet.
This program is quite broada list of features and is also ideal for jokes on friends or experiments. If you have other devices on the web, whether it's computers, phones or tablets, you can do the following with dSploit:
And this is not the whole list of possibilities.

But where to find such hacking programs forhacking? Due to the fact that they can be used by attackers, there are no such applications in official stores, but each program has its own website, where you can download the latest version with detailed instructions.


























