
Since 2014, several new ones have appeared on the Web.varieties of the newest encryption viruses, similar to their ancestor - a virus called I Love You. Unfortunately, the CBF encryption virus can not be decrypted even today by the available methods offered by leading antivirus developers. However, there are still some recommendations for recovering encrypted information.
Today, at least three are known.virus extortionist. These are the CBF virus, as well as the XTBL and VAULT viruses. They behave in almost the same way, offering, after encrypting important files and documents, to pay for receiving a code that could decrypt the data (as a rule, after a message appears on the monitor, a letter comes in requesting payment for decryption services).

Alas, naive users rush to pay the n-th sumor even send examples of infected files to intruders. But if you look, this information is confidential for many companies, and when sent, it becomes public.
The virus itself in most cases penetrates the system through emails received via e-mail, less often when visiting questionable pages on the Web.
Not everyone can notice the emergence of a threat.even the most powerful antivirus package. Moreover, at the earliest stage it is not detected even by portable utilities like Dr. Web Cure It !. Since the virus is self-replicating, over time it seizes the entire system with its tentacles.
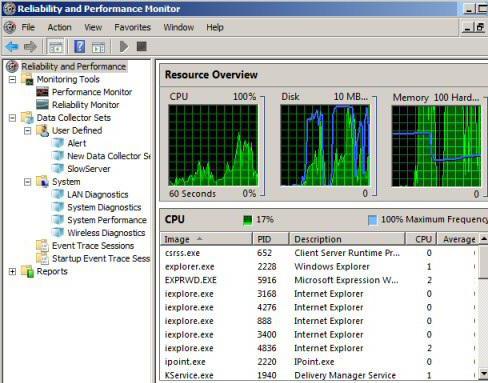
При первых симптомах может сразу же проявиться excessive load on the central processor, as well as unauthorized use of RAM. In this case, for example, when you log into the same Task Manager, you can see a process called Build.exe. By the way, in the main administrator directory or the current user folder, a section of x86 program files is created in which there is a RarLab folder containing the required Build.exe file, checkdata.dif and winrar.tmp. In addition, the Build file also appears on the desktop. Then in the browser used to surf the World Wide Web, images may appear containing porn or links to erotic content sites.
Next comes infection.As a rule, files of office applications like Microsoft Excel, Access and Word are renamed. Also, problems can arise with databases of the .db and .dbf formats (most often “1C: Accounting.” The .cbf is added to the main extension, but it is not possible to read (open) such files, because the CBF encryption virus itself decrypts the infected objects can not (simply can not). What to do in this case?
First, you need to clearly understand what is needed here.act as correctly as possible. If the virus is detected by any software, it cannot be deleted !!! You need to put the threat in quarantine, which is present in almost all applications of this type.
Removal or cleaning will only result inthe main executable elements will disappear, but the encrypted information will still be unreadable. But from quarantine, it will be possible to send a file for inspection to the online laboratory of the manufacturer of the installed antivirus in the system. But this does not always work.
So, the .cbf extension has already been assigned to the files.Depending on the expiration date, there may be several situations: either the files are simply encrypted, or the entrance to Windows is blocked (even the “Desktop” is inaccessible).
Make a reservation immediately:There is no question of any transfers of funds. For starters, it is better to search the databases on the Internet from another computer, which contain most of the known codes to unlock access (you can use at least the Unlocker section on the official Dr. Web site). True, not the fact that such codes will work. You have to treat the system yourself.
CBF-вирус расшифровать (вернее, последствия его effects on files), in some standard way will not work, because it uses a 1024-bit encryption algorithm. If anyone does not know, today the 256-bit AES system is relevant. You can try to restore the original data by referring to Windows Restore.
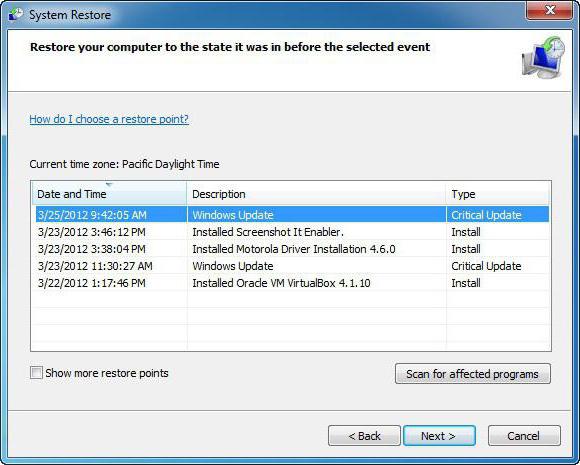
If login is possible, find this section.can be in the "Control Panel" and roll back from the control point prior to infection. If the entrance to Windows is blocked by a message requiring money transfer, you can try to force the computer terminal or laptop to restart several times. This will have to be done until the system “matures” to restore automatically. Naturally, you can try to use the recovery disk, try to perform actions with the command line and completely overwrite the boot sectors, although there is little chance of success. This only works in the early stages when the CBF encryption virus has only penetrated the system or network.
If a system rollback does not help, you should use the special features of restoring previous versions of files that are embedded in the Windows operating system itself.

To do this, through the "Explorer" go toproperties of the selected disk or partition and use the tab of previous versions of files. After such actions, again, you will need to select a control point, then open and copy the necessary files to another location. This method is in many cases more effective.
If we consider the methods proposedAntivirus software developers, you can try to remove the CBF virus extension with the help of special decoder applications (but only official ones, and not user developments like decoders of unknown origin).
However, it is immediately worth noting that they workOnly if there is an installed official version of the anti-virus scanner with the corresponding license key. Otherwise, you can only harm. The virus will simply be removed, after which even the opportunity to contact the attackers will not. There will have to re-install the entire system.
As already understood, the CBF encryption virusit cannot decrypt files infected by it. Separately, it is worth paying attention to actions that are not strictly recommended. Note the most important points:
In general, it is necessary to clearly understand thatIt’s impossible to decrypt a CBF encryption virus on your own. It is better to refer to the official sites of anti-virus laboratories like Kaspersky, where you can leave problem files for analysis in a special section, or send the quarantine file directly from the program.

However (this is approved by all developers)it is better to attach the original to the infected file, if one exists, say, as a copy on some removable media. In this case, decryption will be much easier, although it’s far from the fact that the files needed by the user will be restored.
As a rule, and this confirms the majorityUser feedback, support service is usually silent for a very long time, and if it decrypts data, it concerns single files. And what to do with arrays of tens or hundreds of gigabytes? Such a volume even with the help of special "cloud" services to send, and even more to restore, is simply unrealistic. But let's hope that the developers still find a way to cure infected files and a way to counter the penetration of threats of this type into computer systems and networks.


























